支撑信息化发展 90%
配合企业规模的扩张,实现统一身份、统一应用、统一审计、统一认证及自动化管理能力。
满足远程办公需求 90%
Authing 联合零信任厂商,实现统一认证,满足员工居家办公设备/网络的统认证一管理。
使用产品
统一身份认证
身份自动化
权限管理

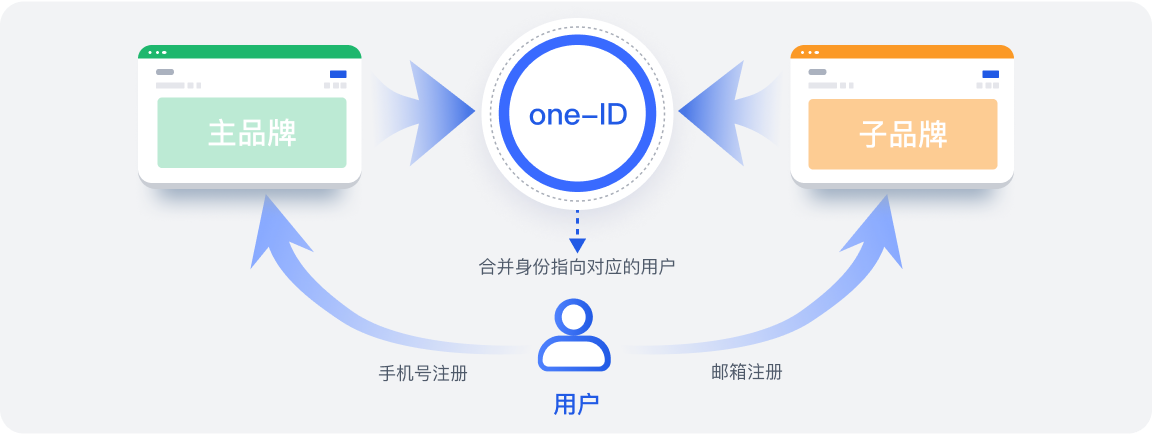
Authing 完善的身份管理后台,能帮助企业快速统一各个系统的身份源,集中管理身份数据。面向复杂的业务场景,还能进一步设置自动化的工作流,自动开通/关闭/冻结账号和权限。
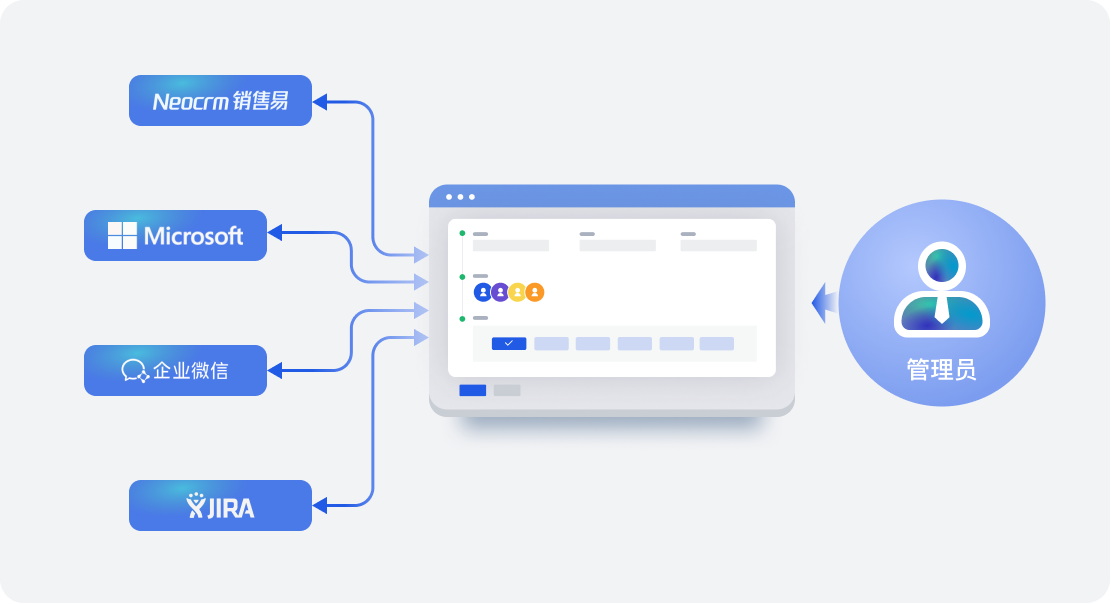
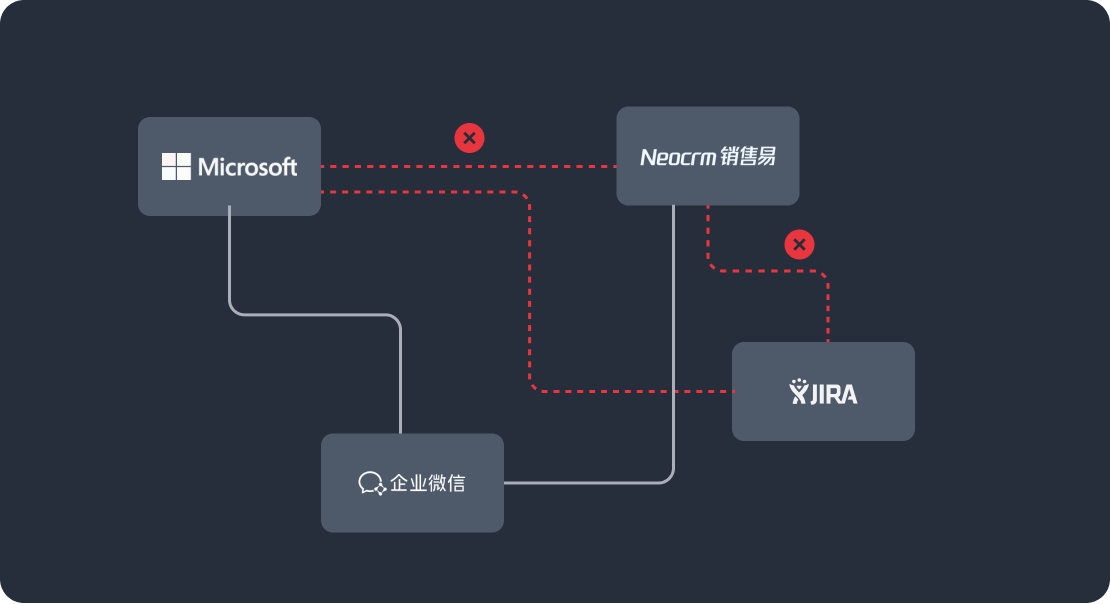
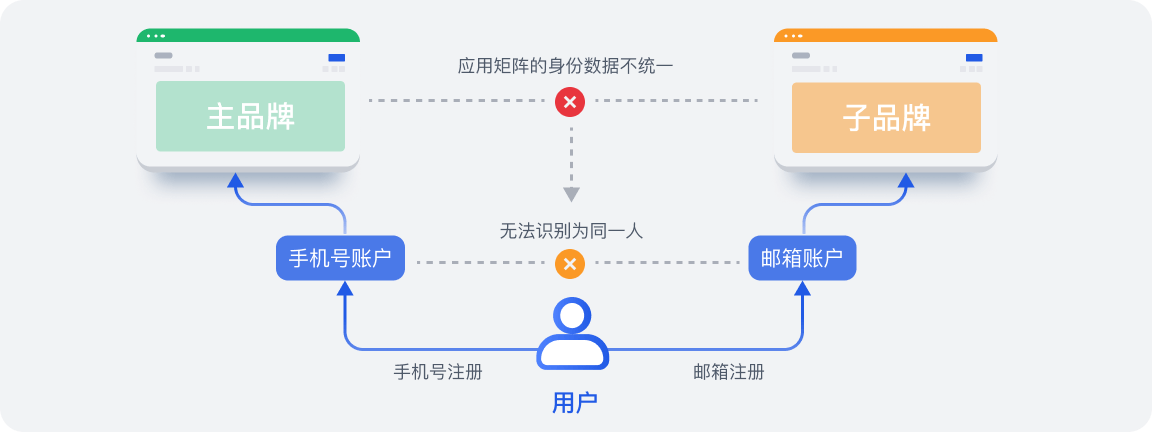
随着企业规模逐渐扩大,应用系统逐渐增多,身份数据割裂,管理越发困难。自研身份管理系统因为缺乏扩展性,常跟不上业务变化,内部信息化人员也没有足够的精力来维护,难以适应企业的快速发展。
import { AuthenticationClient } from "authing-node-sdk";
const authenticationClient = new AuthenticationClient({
appId: "AUTHING_APP_ID",
appSecret: "AUTHING_APP_SECRET",
appHost: "AUTHING_APP_HOST",
});