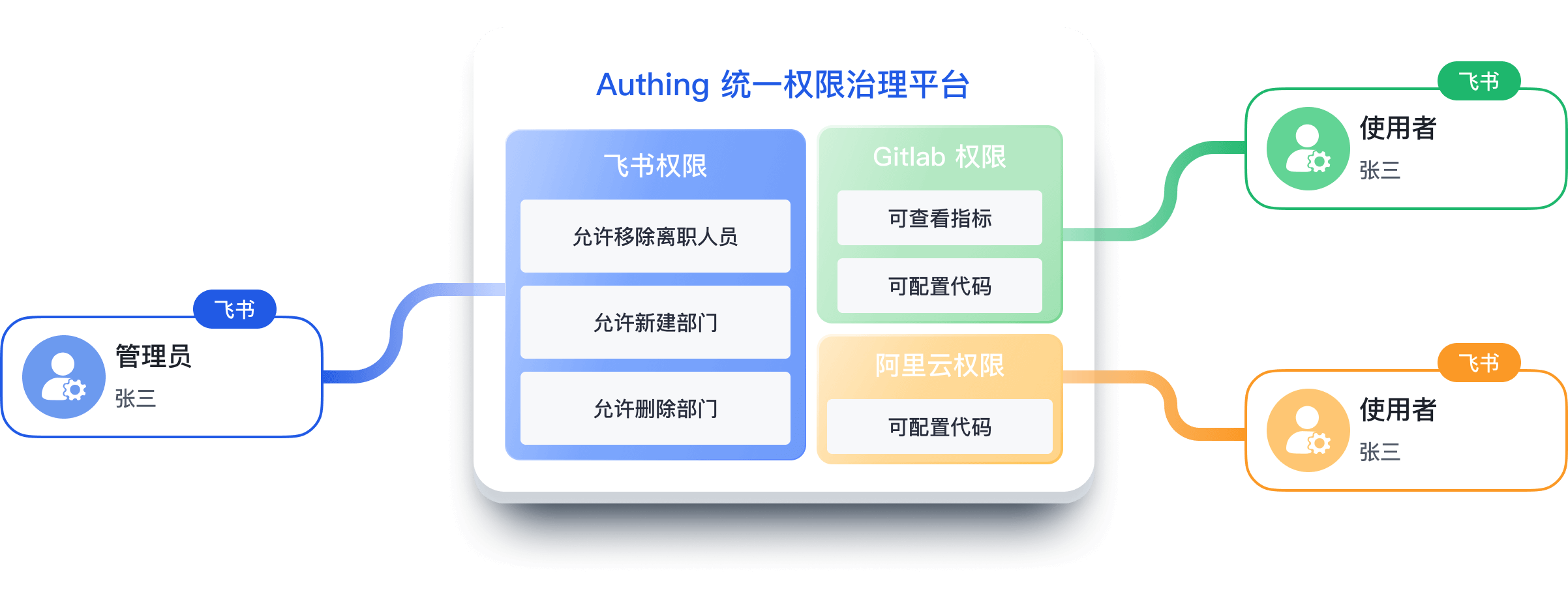
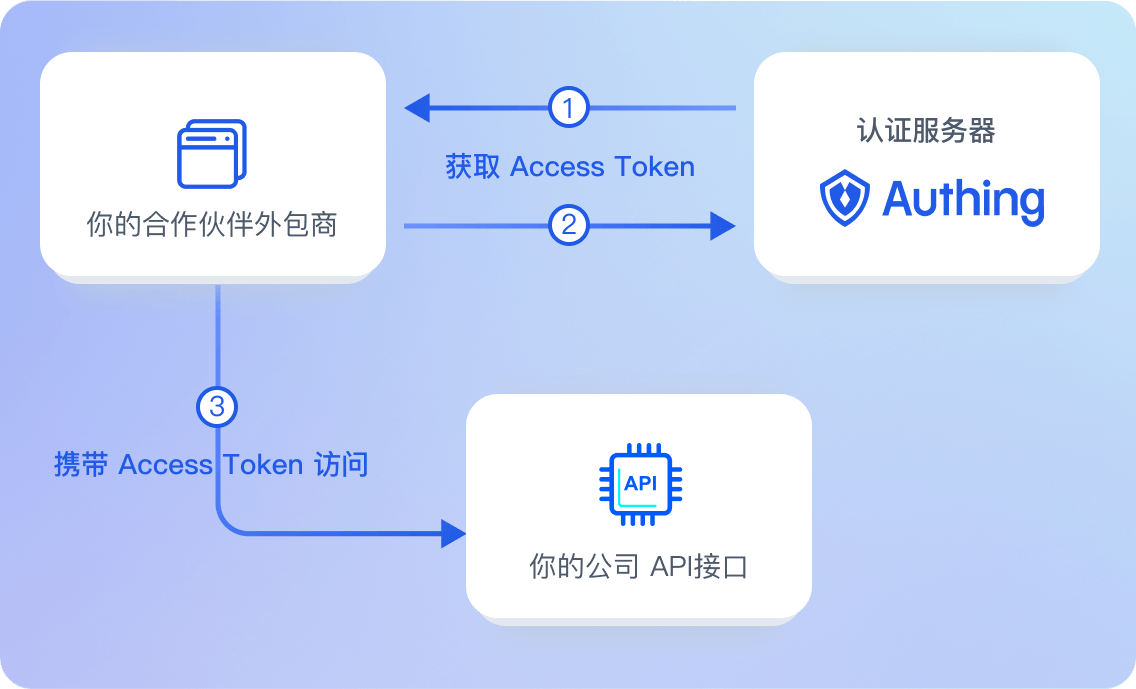
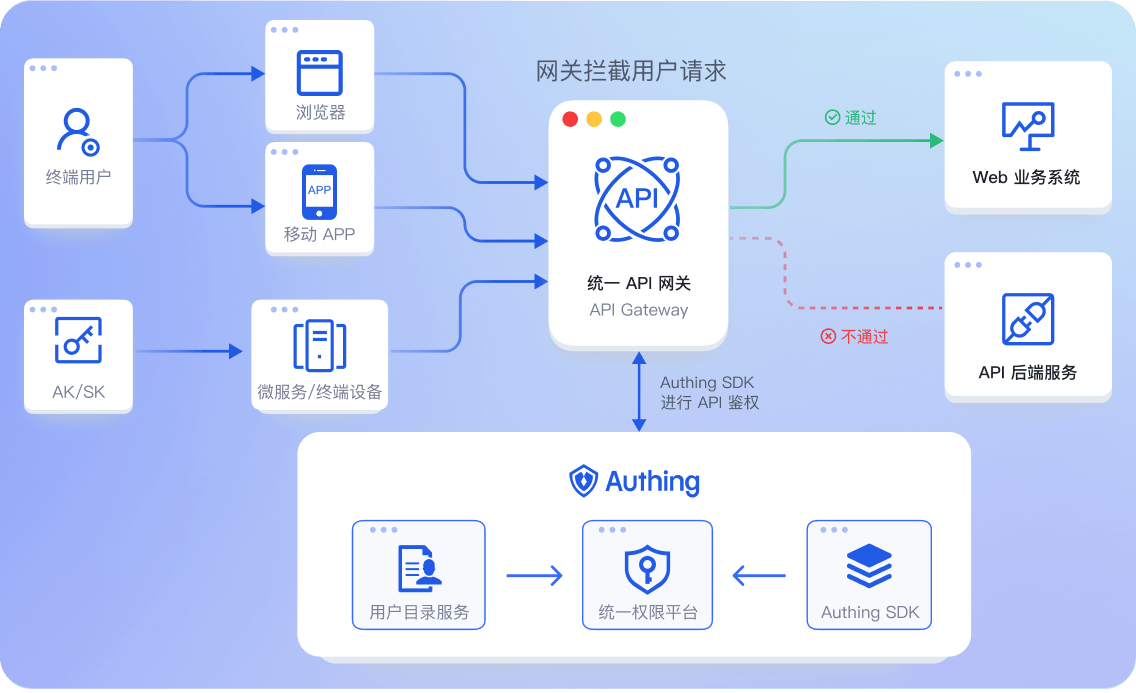
使用 Authing 集中管理各系统的资源权限
减低开发和运维工作量
第一步
快速集成多个系统至 Authing,实现统一权限管理
使用 Authing,企业能将多个不同权限架构的应用轻松集成至一个统一的后台,将各应用的功能拆分为细粒度的资源,即可集中控管各应用下的资源,无需付出额外的应用对接成本。
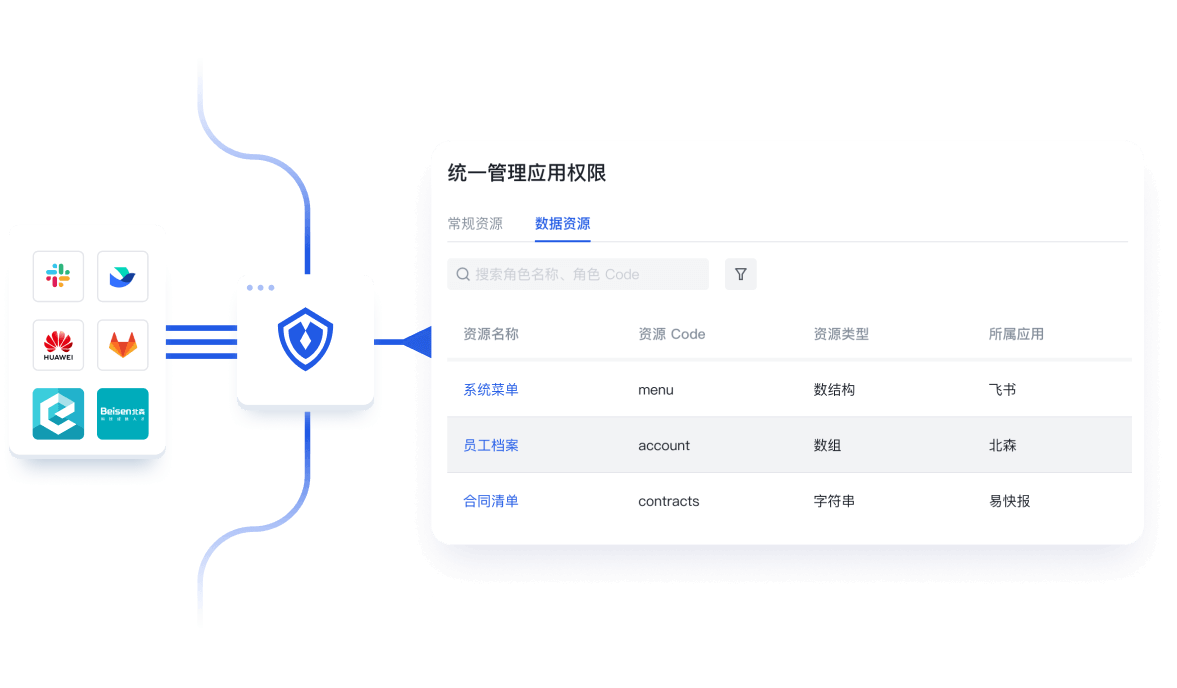
第二步
自定义资源、操作和角色,满足个性化权限管理场景
Authing 支持企业根据自己的需求创建 API、菜单、按钮等资源,定义对应资源操作(如读取、编辑等),以及被赋予权限的主体角色
(职位、项目组、部门等),几乎能涵盖市面上所有权限管理的场景。
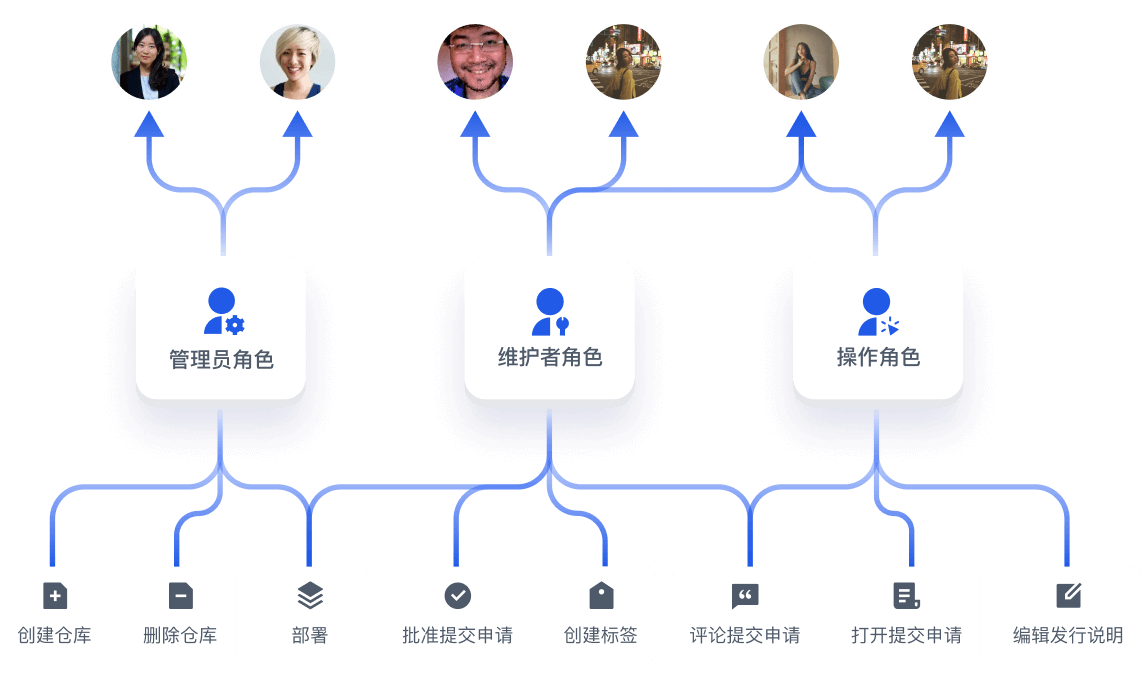
第三步
将资源和操作赋予角色,轻松实现细粒度授权策略
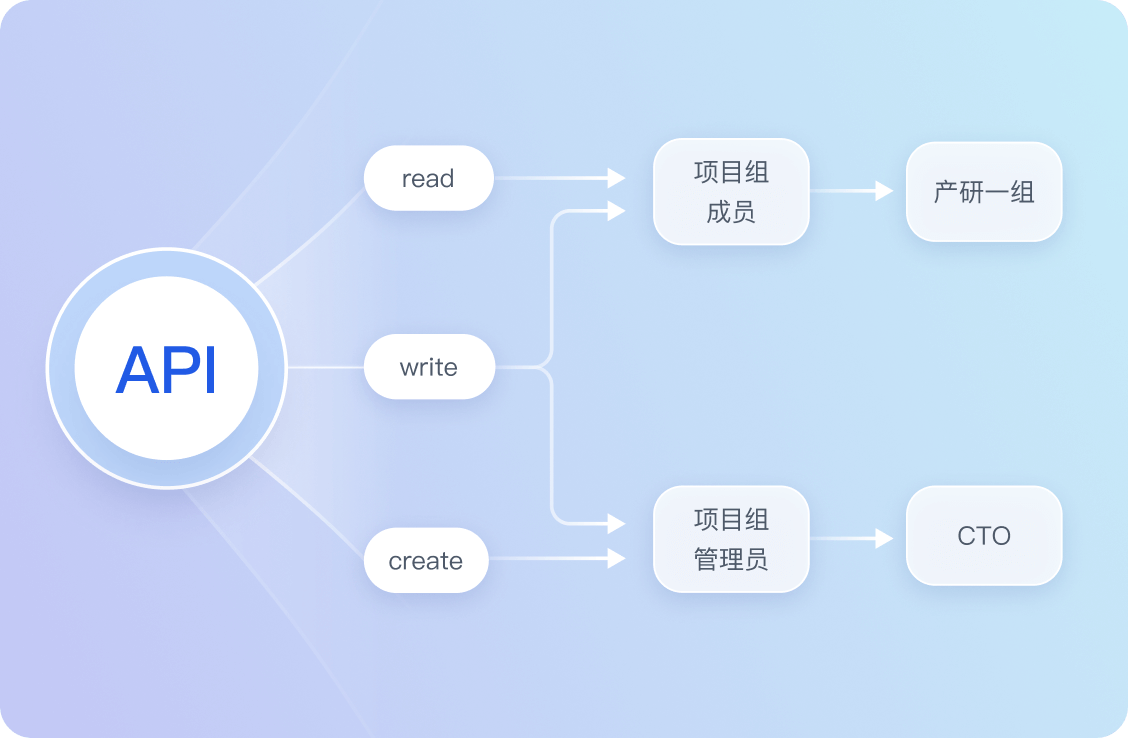
基于角色的访问控制
- 什么是 RBAC
- 面向场景:中小型企业
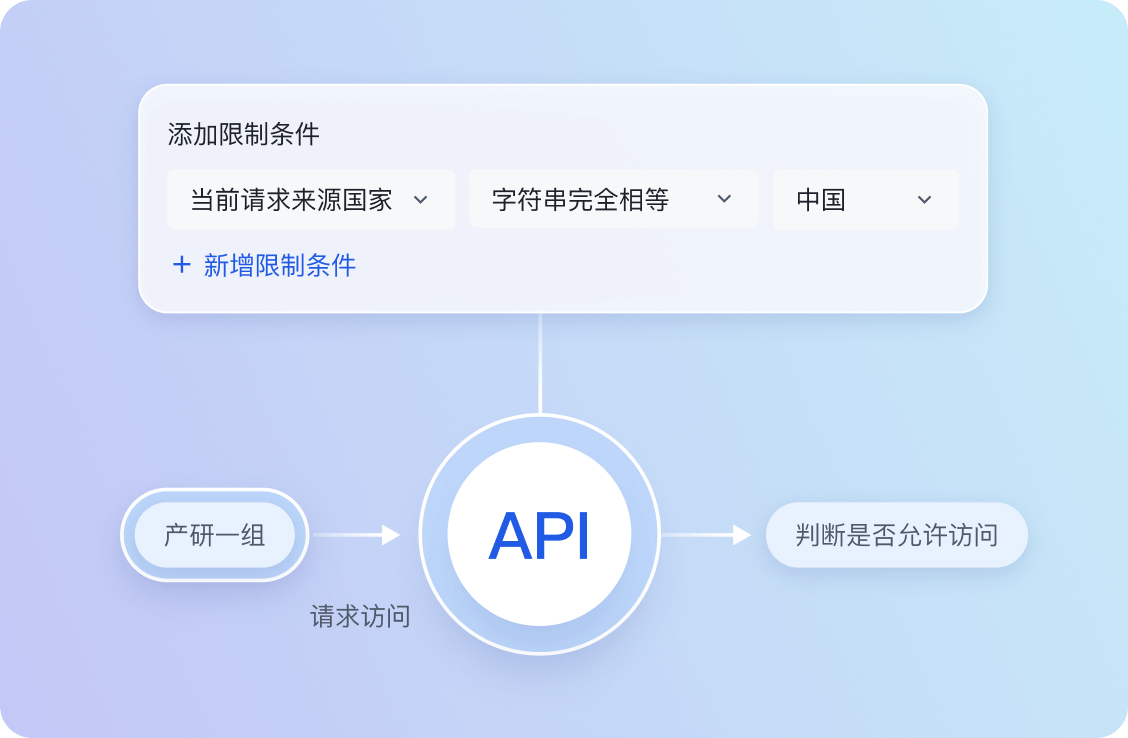
基于属性的访问控制
- 什么是 ABAC
- 面向场景:大型组织
第四步
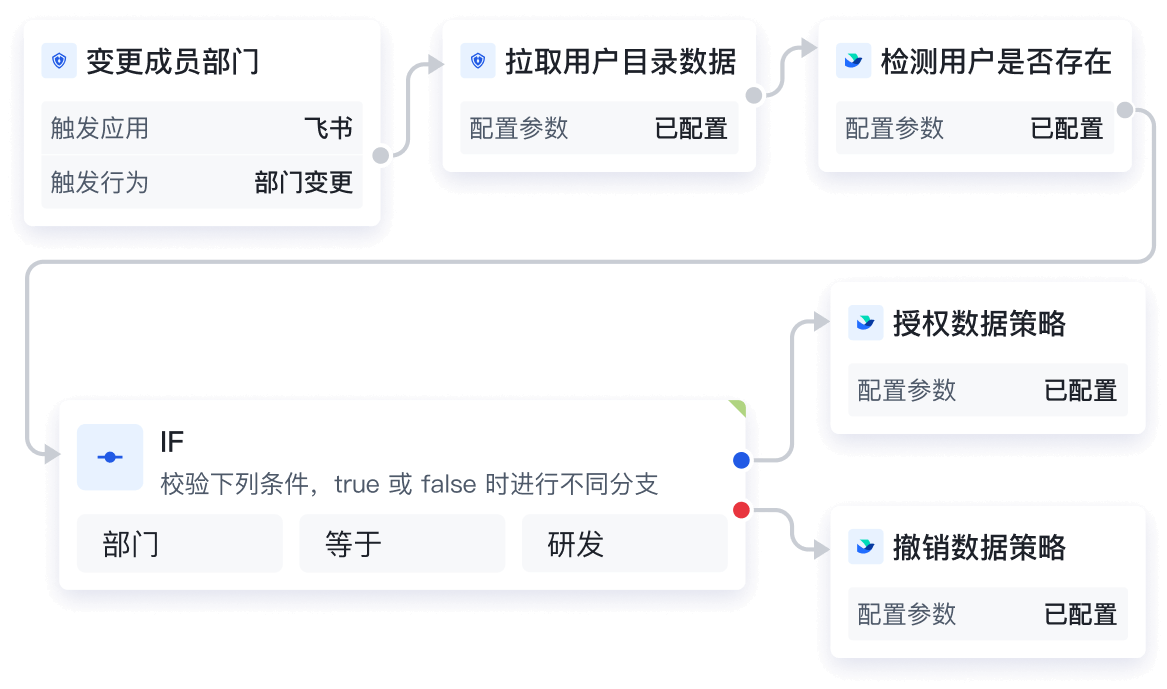
结合自动化能力,减少手动操作的低效和风险
将配置好的权限策略结合 Authing 身份自动化能力,当员工入职、离职或组织架构变动时,
能自动触发管理流程并进行权限的申请、审批、开关,能有效减少管理成本,和漏关/错开权限带来的数据泄漏风险。
第五步
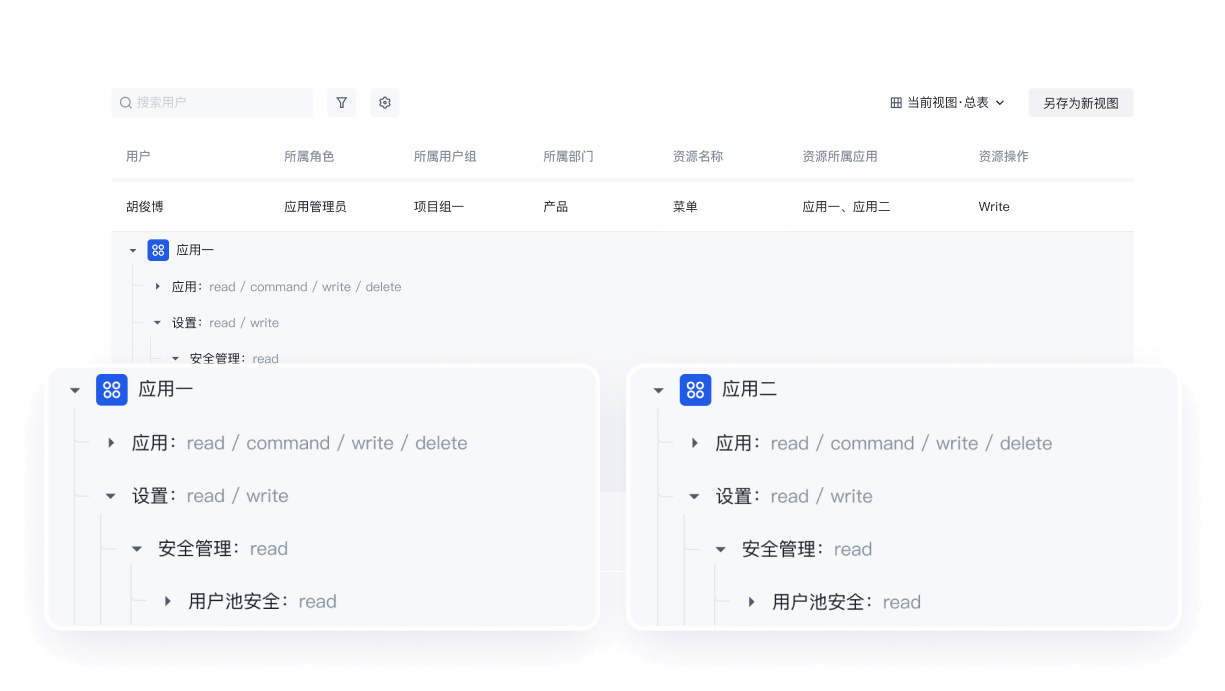
一键生成权限视图,统一查看人员多应用权限
Authing 以用户为单位,提供可视化、全局的权限视图,能展示用户在不同应用下的资源权限和关联策略。
企业可通过筛选生成多个视图,方便事后审计,减少重复低效的工作。